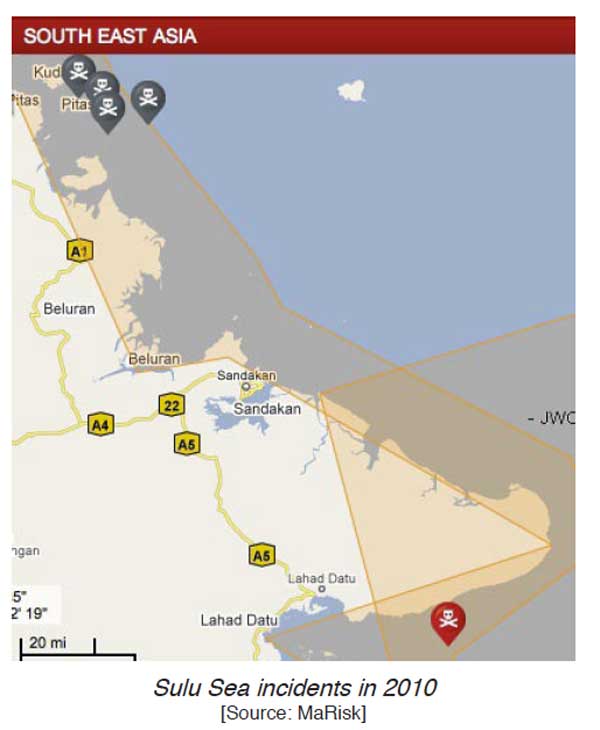
09/22/2011 – During our annual visit to New River to get caught up on Osprey developments, Second Line of Defense sat down with Lt. Col. Boniface who was the XO for the Aviation Combat Element (ACE) for the 26th MEU.
We have published recently an interview with Col. Desens, the 26th MEU commander.
https://sldinfo.com/the-amphibious-ready-group-arg-and-libya/
Here the conversation focused upon the aviation assets used in the operation off of the MEU and notably the Osprey.

Lt. Col Boniface. has a wide range of experience, and having done many deployments on a MEU. His background has been with CH-46 program and has been flying Ospreys for the last three years. He is now Commanding Officer, Marine Medium Tiltrotor Squadron 266, MCAS New River. His personal decorations include the Air Medal Strike/Flight (12), Navy and Marine Corps Commendation Medal, Combat Action Ribbon and the Navy and Marine Corps Achievement medal.
SLD: Some folks consider the Osprey as the replacement for the CH-46 much like some folks consider the F-35B as a replacement for the Harrier. But I believe that this actually distorts the discussion because bringing both planes to the MEU is a gamechanger. What are your thoughts about the process of transition?
Lt. Col. Boniface: The Osprey is clearly not a CH-46. It is an aircraft that can fly like an airplane, but land and takeoff like a helicopter, but it is not defined by its essential ability to operate as a rotorcraft.
In comparison to the legacy CH-46E, I can carry twice as much, twice as fast and twice as long. Actually, in many cases I can almost triple the capability. Finally, it is a more reliable aircraft and ultimately a safer aircraft.
It provides the ability for the PHIBRON/MEU to keep the ARG farther out to sea if needed, thus increasing the element of surprise and keeping us safer too. With the CH-46E, you are typically operating 25-50 nautical miles (NM) from shore. As of today, I can operate 250 NM or greater from shore and I can close this 250 NMs from ARG shipping in just about an hour with 7,000 pounds of Marines, or cargo in the back.
I can actually launch at approximately 52,000 pounds due to the MV-22’s ability to perform a rolling short takeoff (STO) from the flight deck as opposed to the vertical takeoff required by a traditional helicopter.
Bottom line, I can carry more Marines, cargo and equipment, and I can close an objective area twice as fast while staying outside of most enemy weapon engagement zones.
It is a completely different animal. It is a true “game changer.”
SLD: The Osprey is significant in logistics support for the fleet as well which was demonstrated during recent operations off of Libya.
Lt. Col. Boniface: I need to be very clear, the Osprey is not only supporting the USMC, but also supporting the USN-USMC team. During this deployment the USS Kearsarge suffered a mechanical loss of a propulsion screw. We were only able to do four knots through the water; at that point we were 300 miles from land. The only thing we could do was to get tech reps and parts out to the ship to allow us to make a best speed of 11 knots to get back into the fight. Remember you can’t really launch aircraft if you can’t make the correct wind across a flight deck, and you can’t effectively launch Harriers to continue their strike mission with four knots of wind either.
The Osprey was the only bird we could use to close this gap, fix the ship and continue the mission we were executing off the coast of Libya.
The V22 is like driving a Cadillac Escalade compared to your dad’s old truck. I’m traveling better; I’m able to carry more It’s more reliable, and efficient. It’s smoother. It’s safer.
Really comparing the CH-46E to the Osprey is like comparing apples and oranges. With the CH-46E, I am typically flying 300 feet at 110 knots. With the Osprey, I can be at 13,000 feet and flying at 250 knots, all with Marines and equipment in the back. I am flying an airplane, not a helicopter.
SLD: When we were talking earlier, you emphasized that the Osprey’s capabilities compared to the FROG was gamechanging in character. Could you elaborate?
Lt. Col. Boniface: It completely changes the game for the ARG/MEU, it changes the game for how the Marine Corps does business. I didn’t fully realize, nor appreciate this until I was operating in some of these locations during our deployment.
Once we got into the Med for the Libyan operations during Operation ODESSEY DAWN, Naval Air Station Sigonella was our only forward support base.
The Osprey functioned as a force multiplier in these circumstances. I could fly 300 miles plus from the USS Kearsarge to Naval Air Station Sigonella, land, get a quick hit of gas if needed, put five, six, seven thousand pounds of gear, equipment, troops, parts, and be back quickly to the ship within 2.5 hours.
Half of our MV-22s were conducting combat operations in Afghanistan while we were conducting combat operations off the coast of Libya aboard the USS Kearsarge. So you can do the math: Half of the Osprey’s conducting combat operation in Afghanistan and the other half performing combat resupply, and TRAP operations off the coast of Libya.
I wouldn’t have even fathomed this expeditionary and amphibious capability 10 years ago. Also, the Ospreys from Afghanistan flew directly to Souda Bay, Crete and then onto Naval Air Station Signalla, Italy. This trip is a 3500 NM transit. This has been the longest in our short history, and they did it in one day. You can’t even begin to argue or compare and contrast these facts with the CH-46E.
SLD: How important to the operation was it to break the CH-46 tether?
Lt. Col. Boniface: A complete transformation to how we are doing business has been involved. In order for the USS Kearsarge, the ARG and the 26th MEU to stay in their operational box during Operation ODESSEY DAWN, and enable the Harriers to continue their strike mission, we were reliant on other assets to supply us. For many supply items, the Osprey provided the logistical link to allow the ARG to stay on station and not have to move towards at sea re-supply points and meet re-supply ships.
Without the Osprey you would have to pull the USS Kearsarge out of its operational box and send it somewhere where it can get close enough to land or get close enough to resupply ships to actually do the replenishment at sea. Or you would be forced to remain where you are at and increase the time you’re going to wait for this part by three, four days or even a week.
The ARG ships are only moving at 14-15 knots. At best, let’s just say they move an average of 13 knots per hour, and add that up for the 300 miles that you have to sail. Now you’re looking at least a day to get the needed folks, parts or equipment and then the transit time back to the operational box. The V22 will do that in a couple hours and allow the ARG/MEU to keep executing its mission.
SLD: So part of your gamechanging argument is something people do not usually focus on, the use of the Osprey as a backbone of rapid resupply and logistics support?
Lt. Col. Boniface: It was a key performance element. It facilitated the ARG’s strike missions over Libya by allowing the Osprey to perform a combat resupply mission. And it did the other items crucial to the operations such as the TRAP mission and bringing in supplies to keep the Harriers operating. By keeping us within a suitable striking distance, the Osprey helped reduce the AV8-B pilots overall fatigue factor, increase that safety margin and ultimately kill bad guys.
And if the collapse had been more rapid, and we would have needed to put Marines on the ground (for example, a possible humanitarian assistance, disaster relief mission), there is no question that the Osprey would have been central to that effort as well.