“Re-norming” the Asymmetric Advantage in Air Dominance: “Going to War with the Air Force You Have” (Part Two)
By Michael W. Wynne, 21st Secretary of the U.S. Air Force
10/17/2010
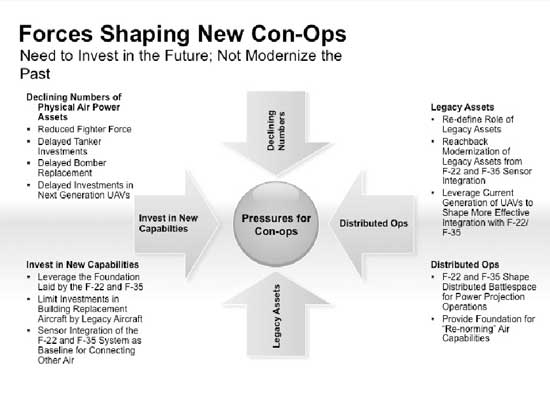
What are the available platforms and technologies that we have invested in to date? And how can we shape effective concepts of operations for a joint and combined air strike force, which leverage these capabilities?
I define joint as involving all available American Air Forces; which would have an intrinsic advantage of interoperability; though our first recommendation to expand the limited tactical cross training that currently occurs, as with the limited set of advanced fighters; this could be a singular mission. I define “combined” as a coalition of the willing; for which for many of our allies might well mean their version of the Joint Strike Fighter; or a very compatible fourth generation fighter aircraft.
In defining tactics, one might recall how even in the Battle of Britain, true integration was far more likely in a tattered set of infantry units than air units. Assuming such integrative capability is a major leap of faith, but may be mandatory as the current Chairmen of the Joint Chiefs admission that future Navy’s may need to operate together as he witnessed the decline of the U.S. Blue Water navy and called for a global 1000 ship Navy.
Combined forces must train together for maximum result. This puts pressure on diplomats to assemble such a combined force; as it puts pressure on the Joint Staff and the combatant commander to allow the air component commander to execute this part of the mission with full joint assets and to have an interoperable force
Though the design engineers and the human factor professionals combine their talents to make fifth generation or advanced fighters ‘easy’ to operate; the book outliers underscored the need for concentrated operator time to truly exploit the enormous capacity we are in the process of fielding with new systems and technologies.
(Credit image: SLD)
The capacity we are fielding can allow the force application designers to devolve more authority to the pilots; the F-35 becomes then the first generation air battle management system. The information age has granted to the computational system all the benefits that the intelligence agencies once husbanded for fusing sensor received information; and the sensor capabilities have offered to the pilot an unprecedented view of the three dimensional battle space.
On top of what the individual fighter asset will be able to do, the ability to interchange information among platforms is a significant bedrock for change in CONOPS. Such a capability will allow the pilot to be a node on the net with an internal router able to receive and transmit information to air operation centers, air operation commanders and combatant commanders.
The capacity we are fielding can allow the force application designers to devolve more authority to the pilots; the F-35 becomes then the first generation air battle management system. The information age has granted to the computational system all the benefits that the intelligence agencies once husbanded for fusing sensor received information; and the sensor capabilities have offered to the pilot an unprecedented view of the three dimensional battle space. On top of what the individual fighter asset will be able to do, the ability to interchange information among platforms is a significant bedrock for change in CONOPS. Such a capability will allow the pilot to be a node on the net with an internal router able to receive and transmit information to air operation centers, air operation commanders and combatant commanders.
Such interactive, distributed capability was once planned for later generations of the F-22; which can play a similar role. Indeed, the interaction between the F-35 and the F-22 in terms of onboard systems is a key dynamic for reshaping air capability, and as the next generation of remotely piloted aircraft gets added to the mix, we will have a strong baseline for “renorming” air operations. The technology for this is widely known; and available for incorporation.
But several key questions need to be resolved and challenges met to leverage the new capabilities inherent in the new technologies.
- Now that the nation has minimized the quantity requirement, will it maximize the opportunity for interconnectivity and thus the quality of the force?
- What will be the training opportunity for the interconnected air fleet, with the Navy model of three months to interconnect a battle group?
- Will the interconnects include our allies to get in the air what the JCS Chairman once quested for on the sea; a thousand ship Navy?
Such shared and congruent capability truly assists in managing sensory overload as the system can establish ‘chats’ and the displays automatically integrate inputted targeting information. What is available is target cataloguing such that the air operations center can optimize the available shooters to fulfill target opportunities.
The sensors can be easily extrapolated to ‘see’ moving targets versus stationary; but the system must off board and discard these such that the principal mission set is executed. air operation commanders can reset the mission set; but this must be accomplished as well in the pilot’s seat; as if all the participants are acting together.
In past engagements, there has been a debate as to how to best penetrate enemy airspace; stealth was considered by some a ‘silver’ bullet strike system sufficient for executing such a mission. But, as historians have told us over the decades, the enemy has a vote in the development of the battle. They are also planning to shape the battle to fit their designed response.
Under current thinking, American planners called for increases the quantity of penetrators to meet global competitors, and for co-opting the integrated air defenses. Given the current forecasts for platform numbers, this will not be achievable. Different strategies, and different tactics will be required to deal with integrated air defenses, such as capabilities to expose these defenses in ways that allow the penetrators to shape the battlespace.
During past conflicts and even into more modern era, “reconnaissance by fire” was a method to draw out enemy positions by convincing them they had been discovered and were being killed; therefore they would strike back and reveal themselves. During the Vietnam era, the air battle became precarious for the slower AC-130 aircraft, which became targets as they performed their nightly missions. Lighting up when they commenced firing, and thus being shot at by enemy anti-air batteries.
A technique they developed to silence or slow the response was to fly a two-ship circle; where one ship would light up and intentionally draw fire from the ground units; thus allowing the other to target the battery before it could silence and move. Extending this on-off technique from the AC-130 Gunships to induce elements of the modern integrated air defense mechanism to reveal itself and its tentacles by offering a ripe target so as to trap an air defense system into giving up its location, or sensor; or communications system to sensors, and ultimately to shooters.
An advantage that the AC-130 aircraft brings to the fight is the closed form “kill cycle,” which when operating in a free fire zone allows the OODA loop to be milliseconds in length. Tacticians and strategists need to keep this in mind as they lay traps for integrated air defences; which will smartly be hidden in locations which will give pause to central commanders.
From such a perspective, we can see great utility for unmanned or remotely piloted systems. The carriage of weapons in fifth generation aircraft is both limited and limiting. Pilots who are the first to launch expose themselves in a dramatic way; and one must presume that once exposed the probability of survival diminishes.
Again, one must see stealth as shelter from the enemy, prolonging the exfiltration of intelligence and reducing the probability of mission failure, not as a medium to enhance the probability of success for the individual fight. We need to think in fleet terms operating in a distributed battlespace. Once we make the mental leap, the air battle manager construct can move into the cockpit where the pilots are part of a team that can become the closed form kill chain and turn the weapons to target time within the enemy’s cycle.
One must see stealth as shelter from the enemy, prolonging the exfiltration of intelligence and reducing the probability of mission failure, not as a medium to enhance the probability of success for the individual fight. We need to think in fleet terms operating in a distributed battlespace. Once we make the mental leap, the air battle manager construct can move into the cockpit where the pilots are part of a team that can become the closed form kill chain and turn the weapons to target time within the enemy’s cycle.
Planners need to turn their attention to providing support to the air battle manager that has taken up a position of control; and has managed to maintain concealment at the same time. Therefore, we need to consider how to absorb and catalogue appropriate targets to achieve the mission; and then exhaust the missile load of an unmanned vehicle (e.g. Winchester) even fast and stealth managed.