By John Wheeler
cy*********@*****fo.com
John is writing a weekly column dedicated to the cyberspace domain: he will continue to provide regular insights into how to shape effective con-ops in the cyber domain and craft a Terms of Reference for facing XXIst Century cyber challenges.
John has a wide range of combat and government experience. He is a West Point graduate with warfighting experience in Vietnam. He has significant private sector experience, as well as holding various positions in government, including being Secretary, US Securities and Exchange Commission. His most recent position as Special Assistant to the Secretary of the Air Force included principal tasks, among which were standing up Cyberspace Forces and placing Precision Strike technology and Real Time Streaming Video targeting links into the hands of groundfighters in combat.
***
Welcome to SLD Cyberpoints Weekly Column
George Santayana wrote, “Only the dead have seen the end of war.” In Cyberspace he will certainly be proved right, and in the minds of many who watch the predations going on in Cyberspace upon Corporate, Military and Personal data bases, he has already been proved right.
In ways similar to the evolution of the Undersea Domain in the early 1900’s and the Air Domain in the 1910’s and 20’s, the Cyberspace Domain is being developed and discovered, with the military implications still at a very young stage. There abound policy and technical, training and recruiting, equipping as well as doctrine questions in large number. Huge contracts for Cyber are being let by Government and Industry.
“Cyberpoints” is meant to take a weekly look at an issue or event in light of the larger flow of development of the Cyberspace domain. Input, tips, heads-up, comment and correction are most welcome.
New books, articles, pending legislation, needed legislation, Corporate pronouncements, DHS, State, DoD, VA and other Agency Cyber Matters are all of interest. Cyberwar is not the only thread; Cybersecurity for Corporations and Individuals is a core topic, as is the way each of the tools of diplomacy and war can combine and impinge as to Cyberspace.
For example, when the Secretary of State says that the United States is committed to “Freedom of the Internet”, that means, really, “Freedom of Cyberspace”, invoking the history, heritage and heavy freight of the doctrine of “Freedom of the Seas.” There is plenty of policy work to do and unfold as to “Freedom of Cyberspace.”
***
Cyberpoints No. 2
March 4th, 2010
There are two big topics for this week’s Cyberpoints:
- Two New Cyber Statements: the first by Admiral McConnell; the second by TRADOC about the Army’s way-ahead for Cyber
- Recruiting for Cyber Careers in the military: how effective?
***
I. TWO NEW CYBER STATEMENTS
Two noteworthy Cyberspace statements have been made in recent days.
Admiral Mike McConnell (Ret) published as good an articulation of the need to stand up a robust US Cybercommand as has been made.
We can declare Admiral McConnell’s statement to be the high water mark of warnings about the need for robust Cyber standup. The need now is actual progress, and as much public disclosure of US capability in Cyber as is prudent and possible, for potential recruits and their families. Cyberspace is ultimately a Warfighting Domain as well as a Commercial and Intelligence Domain. And in the end, with war as arbiter, it is the US Military Services that will be challenged to preserve Freedom of Cyberspace, just as long ago the US Military Services established Freedom of the Seas. As noted in this space, George Santayana said “Only the dead have seen the end of war”, and the dictum applies in Cyberspace.
 In addition, the Army has published guidelines for operations in Cyberspace, Tradoc Pamphlet 525-7-8, “Cyberspace Operations Concept Capability Plan 2016-2028“.
In addition, the Army has published guidelines for operations in Cyberspace, Tradoc Pamphlet 525-7-8, “Cyberspace Operations Concept Capability Plan 2016-2028“.
Noteworthy is that the taxonomy used by the Army is shifting to the 21st Century “Cyberspace” terminology and away from the 20th Century labels of “Network Operations.” Language can govern and always influences thought and action. Beady-eyed cowhands from Texas now say, using the Army for example, and with a smile, “OK, the Army has the Cyber Hat. Let’s see the Cyber Herd.”
***
II. RECRUITING FOR CYBER CAREERS: MOM LOOKS FOR CYBER CAREER FOR HER DAUGHTER AND SON
Speaking of the matching the Cyber Hat with a Cyber Herd: How is USA Military doing?
- Some more clarity and inclusion of Cyber Officer and Enlisted Career lanes on the Service Websites will assist potential recruits and their families.
- A quarterly Table of Officer and Enlisted Accessions 2008, 2009 and so far in 2010 in Cyber careers will help track the US Military standup in Cyber. The same is done in other career fields. DoD, with Army, Navy, Air Force, Marine, and, with coordination, US Coast Guard and also US Merchant Marine, can prepare the summary tables. In the Military Lane, in contrast to the Intelligence Lane, this data is traditionally gathered and made public for reasons of transparency to the public and Congress and as deterrence.

MOM LOOKS FOR CYBER LANES FOR HER SON OR DAUGHTER
A good way to think of the effectiveness of military recruiting messages and websites is to think as a Mom-Looking-to-Help-Her-Teens. That is, imagine a Mom, likely a single Mom, trying to sort out good opportunities for her son or daughter. She is a smart hardworking single mom Out in America who happens to see a military cyber story and thinks, “Hey if my daughter Clarita went into Cyber, she could be a sergeant or an officer and her career would be good, she is so good at math” and then the Mom wanders from recruiting office to recruiting office and finds no joy …
Let’s imagine she has heard of Cyber opportunities in the military and has enough life experience to know that a military tour opens many doors in life and work. So in our Mind’s Eye think of that Mom, with a few spare minutes, trying to find where to send young teen daughter or son to talk about Cyber enlistment or Cyber careers as an officer.
Google will send the Mom to the Military recruiting websites. So the searches below are as a Mom might do. And here is what Mom finds:
(a) Mom Goes to The Military Service Web Sites
Opening the sites and then using the Search box in each does not yield a Cyberspace enlisted and officer Cyber Careers list.
http://www.goarmy.com/#/?marquee=officership&channel=careers
(b) Mom finds the Mission Statements in Cyber Commands
- 24th AF: “The mission of the 24th Air Force is to develop, integrate and command and control robust cyberspace forces and operational capabilities to establish, maintain, defend and operate within the cyberspace domain to support Joint Force Commanders across the full range of military operations.” (http://www.nsci-va.org/CyberPro/SeniorLeaderPerspectives/2009-04-23-Col%20Jodine%20Took%20Q&A.pdf)
- 9th Signal Command: “9th Signal Command (Army) operates, maintains and defends the Network Enterprise to enable information superiority and ensure the operating and generating forces freedom of access to the network in all phases of Joint, Interagency, and Multinational operations.” (http://www.netcom.army.mil/about/docs/NETCOM_Pamphlet.pdf)
- Tenth Fleet: Mission Statement not on google. CNO on the Tenth Fleet:
http://74.125.113.132/search?q=cache:8NtQGe-FunkJ:www.navy.mil/navydata/people/cno/Roughead/Speech/10.01.09_CSIS%2520remarks%2520FINAL.doc+cno+tenth+fleet+cyber+dominance+dominant&cd=1&hl=en&ct=clnk&gl=us&client=safari
NOTE THAT CNO SETS “DOMINANCE” IN CYBERSPACE AS THE OBJECTIVE.
There is a debate afoot as to whether the USA can dominate in Cyberspace, and yet, the Mission of the US Military is to dominate the foe, first with deterrence, and then, with the dominant, “unfair” fight.
The Wynne Doctrine, after SECAF21 Michael W. Wynne: “If you are ever in a fair fight, senior leaders have failed you.”
(c) Then Mom Finds Out
- USCYBERCOM No Mission Statement yet for USCYBERCOM it seems. From SECDEF Order to Stand Up USCYBERCOM: http://publicintelligence.net/establishment-of-a-subordinate-unified-u-s-cyber-command/
The Mission implicit in the SECDEF Standup Order for USCYBERCOM is, notionally,“The mission of USCYBERCOM is to guard Freedom of Cyberspace by dominating, deterring and defeating foreign cyber incursion on the United States, her allies, and citizens and by aiding law enforcement, first responders and allies.”
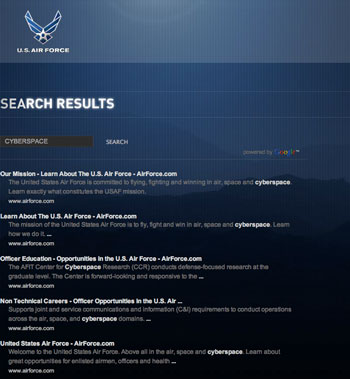
- At this time, only the Air Force site, http://www.airforce.com , has CyberCareers presented, when “Cyberspace” is entered as a search term in the “search” box of each of the sites of the four Services. Only enlisted Cyber Careers are presented. On www.airforce.com, under Officer Careers, no Cyber Careers are presented. A useful report would be a full apples-to-apples comparison of the services as to cyber personnel. The report has to include cyber-personnel detached and serving NSA and other Black agencies. Course listings and majors from each of the Five Federal Academies on Cyberspace are a basic tool for measuring Service posture on Cyber. As well, from the War Colleges and continuing education schools of each Service. This, above all, is basic, knit-one, purl-two info. Essential. Muscling-up in Cyberspace means muscling-up in accessions and careers and retention. Tracking this data is essential for policymakers and the media.
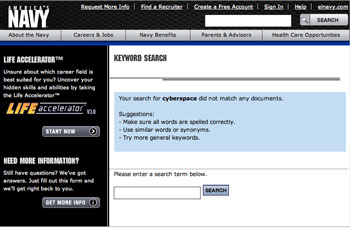
- As with Navy and Army, no hits on “Cyberspace” in Search in: http://www.marines.com. “CYBERSPACE” No results matched your search. Try again using more general terms, for example, if you searched for “famous battles,” try “battles.”
- Coast Guard has Computer and Information fields listed: http://www.gocoastguard.com/find-your-fit/officer-opportunities/career-fields
More clarity in the recruiting websites for our imagined Mom will make recruiting easier and America’s Moms happier.
NOTE: A wide Google search finds statements by the Services on Cyber that do have information for our “Mom” — but they are not consolidated in the Recruiting Sites above. All this is easy to package and correct for the websites, for the Mom — and Dad — and prospective recruit who wants the full picture on Cyber career opportunities. The info and personnel policies are in place; the task is to package and present in intuitive easy form for Americans to check out, e.g.:
http://www.google.com/search?hl=en&q=navy+cyber+recruiting+data&aq=f&aqi=&aql=&oq=
http://usarmy.vo.llnwd.net/e1/soldiers/archives/pdfs/mar09all.pdf
http://www.google.com/search?hl=en&q=army+cyber+recruiting+data&btnG=Search&aq=f&aqi=&aql=&oq=
http://www.airforce-magazine.com/MagazineArchive/Pages/2009/June%202009/0609cyberpatriot.aspx
———-
***Posted March 3rd, 2010